Develop Digital Solutions that Work on an Enterprise Content and Experience Platform
Plan. Code. Build. Test. Deploy. Release. Upgrade. Integrate.
From smart devs, for smart devs.

Less Code. More Technology. Superior Tools.
High productivity and interoperability. Automated deployment and shorter time to market. Platform flexibility. Operational efficiency and high performance. Tighter security and easier maintenance
High Productivity
- Hybrid Headless
- Low-code Integrations
- Powerful APIs
CTs, Module Builder
- Custom CTs
- Sitefinity Module Builder
- Provider Model
VSIX
- Visual Studio Integration
- Open sourced in GitHub
- Sitefinity CLI
Templates, NuGet
- Extendable Data Model
- Sitefinity NuGet Repository
- Content APIs
MVC
- High-performance
- Full control over markup
- Frontend flexibility
ASP.NET Core
- Separate Presentation
- ViewComponents
- JSON page meta-model
Web UI Framework
- Styling & Templating
- HTML, CSS and JavaScript
- AngularJS
Mobile First
- Bootstrap Out-of-the-box
- Responsive Design
- Resource Packages
Decoupled Architecture
- 3-tier architecture
- API-driven content management
Robust APIs
- Content, presentation, and personalization APIs
- Multichannel content delivery
CI/CD
- Advanced DevOps
- Reliable code promotion
- Zero downtime
Connectivity & Extensibility
- Built-in connectors
- Add-ons and integrations
- Service Hooks
DXP Spotlight
Add a Chatbot To Your Website
The Sitefinity Connector for NativeChat makes chatbot integration a breeze. Easy to build.
Easy to train. Easy to theme and customize. Drag and drop to any Sitefinity page to personalize conversations and shape the journey to accelerate
pipeline.
Create. Accelerate. Optimize. Sitefinity Puts The
Right Tools in The Right Hands.
A platform that fosters cross-team collaboration free of bottlenecks. Developers have all the right tools to empower marketers to work independently so they can focus on mission-critical tasks instead.
Textbook Content Governance
From single sign-on through role-based permissions to reliable and transparent content ownership and revision history, reap the benefits with no implications on performance and zero bottlenecks.
Popular Features
- Multisite and multidomain support
- Multilingual support
- SiteSync for content promotion
- Azure AD, custom identity providers
- Workflows
Stellar
Performance
Superbly equipped for enterprise-grade performance, scalability, availability and efficient use of resources. Advanced toolset including CDN, load-balancing and distributed cache.
Popular Features
- Load Balancing
- Advanced Caching Tools
- Site Warmup
- Pre-compilation
- SSL offloading
Maintenance &
Admin Tools
Maintain, troubleshoot and optimize like a pro. Use the rich system monitoring and error logging options to your advantage. Make the most of the built-in tools and capabilities and keep your assets in prime shape.
Popular Features
- Audit trail module
- Health check service
- Performance Diagnostics module
- Built-in Search widgets
- Integrated SEO tools
Built-in and Third-Party Integration Options
to Boost Productivity
Vibrant ecosystem. Rich data connectivity. Boost productivity and increase power and functionality. Resolve data silos and integrate with multiple CRM, ERP, MAS, DAM systems.
Tools & Architecture
Conceived and developed as a platform for scalability and growth, Sitefinity boasts a rich set of contemporary tools to automate, extend and enhance, including a RESTful Web Services API.
Built-In Connectors
A wealth of built-in marketing automation and system integration options to explore and boost productivity. Unlock the full potential of a superbly connected platform and your marketers will love you for it.
Popular Features
Sitefinity Marketplace
Sitefinity Marketplace is a collaborative resource for users letting you easily share and download solutions that enhance the Sitefinity experience. Boost your solution with powerful add-ons and integrations.
Popular Features
Deploy Anywhere. Scale at Any Time.
Enterprise-Ready
Deploy locally and enjoy the multiple benefits of a superbly equipped, enterprise-ready CMS. Load balancing, high performance and availability, advanced caching tools and enterprise-grade security with multi-site and multi-lingual support.
Popular Features
- Multi-Regional Deployment
- Multilingual Support
- Multisite Support
- Azure AD B2B
Sitefinity Cloud
A full Platform-as-a-Service hosted on Azure, Sitefinity Cloud delivers a set of modern DevOps services and workflows to enable the IT organization to plan, collaborate, test and ship faster. Scale your business fast and support large-scale projects.
Popular Features
- Fully-managed PaaS
- No infrastructure and maintenance overhead
- 99.9% Uptime SLA
- Secure, high-performing, scalable
Custom Cloud
Host your Sitefinity projects on Azure or Amazon Web Services and leverage the power of a top-grade commercial cloud. Take advantage of the premium infrastructure and services to deliver both client-side and server-side performance.
The Frontend Development Future. Now.
Don’t get trapped into legacy tech stacks. Tap into a wealth of technology-agnostic content. Code and deliver faster, across platforms and devices.
ASP.NET Core
New ASP.NET Core renderer and
frontend development suite
- API-driven
- Optimal Performance with native MVC
- Cross-platform
Page layout API
- Create and consume content using OData protocol
- Uncapped development potential and FE versatility
- Omni-channel delivery: SPAs, mobile apps
New Page Editor
- Reimagined page and layout builder
- Completely new concept of “sections” based on Bootstrap 4
- True WYSIWYG experience
- Enables editors to build pages in no time
Decoupled by Design
Sitefinity is an API-driven platform and enables distribution of content to multiple systems via REST for a wealth of integration and extensibility options.
- Play to the development team’s strengths
- Not bound by a specific tech stack, you can use the latest frontend framework and UI technology
- Separation of Concerns
- Content management decoupled from presentation
- Content delivery to a broad set of enterprise apps
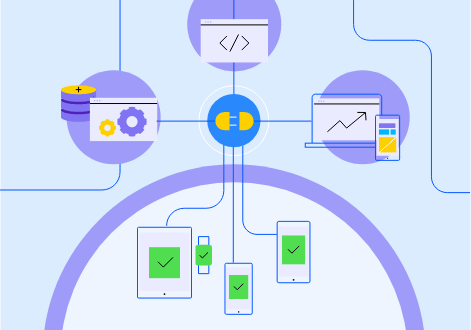
Develop. Deploy. Maintain. Extend. Go!
When duty calls, choose an extensible, connected and scalable platform. Enable marketers to manage simple websites, multichannel content, epic digital experiences and everything in between.
Easy to Develop
-
Built for extensibility, interoperability, integration and flexibility
ASP.Net MVC, VSIX
Web services, Dynamic Content Types
Module Builder, Custom fields
-
Simplified application development, full control of markup, Bootstrap 4, mobile first. Open source widget repository
Resource Packages, Layout Files, Widget Templates
High Customization, .NET Core, Angular JS
High Performance
-
Load Balancing
-
Performance Optimization
-
Distributed Cache
-
Site Warmup, Pre-compilation, SSL Offloading
-
System Monitoring and Logging
-
Performance Diagnostics Module
Effortless Upgrades & Maintenance
-
Continuous Delivery
-
Content Staging and Workflows
-
Languages and Multi-lingual Support
-
Sites Module and Multi-site Management
-
Built-in Search Widgets
-
Integrated SEO Tools
Wealth of Integrations
-
RESTful Web Services API using the OData Protocol
-
Sitefinity Marketplace & Marketing Automation
-
Built-in Connectors
-
Add-ons and Integrations
-
Web Hook
-
Sitefinity Insight and Personalization
Automated Deployment
-
Install via NuGet
-
CI / CD Pipelines
-
Automated System Upgrades
-
Local Deployment
-
Sitefinity Cloud
-
Custom Cloud
Secure by Design
-
Authentication and Identity Management
-
Cloud Operations Security
-
Customer Data Protection
-
Standards Compliance
-
Mandatory code and security reviews, incident management
-
Stellar Support
User Testimonials
I really appreciate the UI that makes it easy to build new pages, drag content modules into them, and architect the structure of the site and the configuration options needed.”
Sean P
Software Development Director
Related Resources
Sitefinity Consulting Services and Training
Transform your Sitefinity digital experience with consulting services from a Progress partners, on-demand and instructor-led training and certification to create a modern, adaptive and customized platform for marketers and developers.
Consulting Services